How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
All Linux and Unix servers are managed manually or by automation tools such as Ansible using ssh. For example, say you have a server at Linode or AWS. Then you copy your public ssh key to a remote cloud server. Once copied, you can now login to those servers without a password as long as ssh keys are matched. It is the best practice. Unfortunately, you are not protecting ssh keys stored on a local desktop or dev machine at $HOME/.ssh/ directory. If your keys are stolen, an attacker can get access to all of your cloud servers, including backup servers. To avoid this mess, we can protect our ssh keys stored on local dev/desktop machines using physical security keys such as YubiKey.
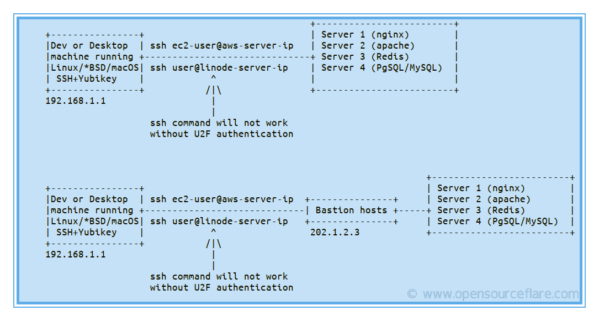
In both cases, you need to insert your YubiKey (or any FIDO2 compatible hardware key) into a USB port and complete the authentication. In other words, ssh login will not work when malware or attacker has stolen your passphrase and ssh keys as they can not insert YubiKey and press the button on it to complete OTP for ssh keys.
In the corporate environment, we have a bastion host that allows ssh access with Yubikey. It is a special-purpose server on a network specifically designed and configured to withstand attacks. The server generally hosts an sshd process, and all other services are removed. Once logged into bastion host, you can access all other cloud servers easily.
Love this? sudo share_on: Twitter – Facebook – LinkedIn – Whatsapp – Reddit
The post How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2) appeared first on nixCraft.